Be part of the new Digital Era
Explore how you can bring more secure and convenient digital interactions to your users and partners.
















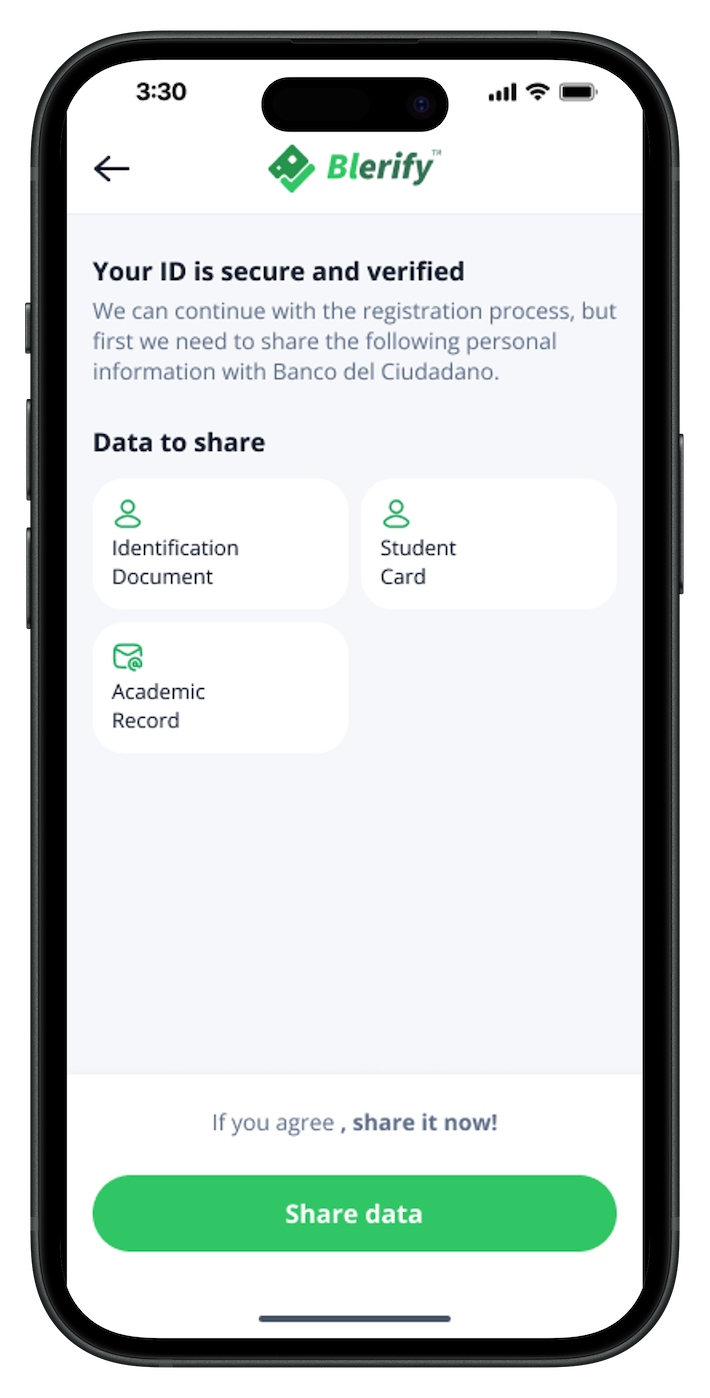
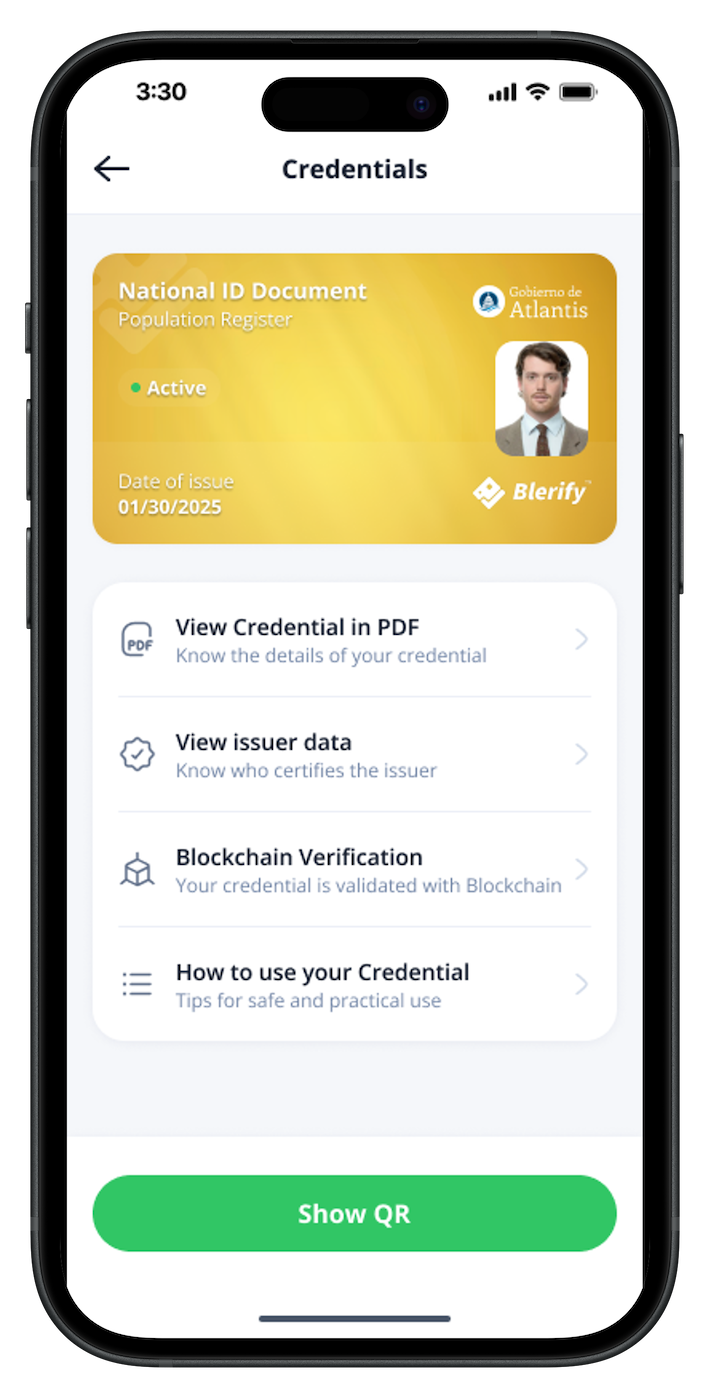
Issue digital credentials to users, employees, or citizens replacing usernames, passwords, security questions, and even biometrics. With a quick QR scan, they share only the data that’s needed securely and instantly.
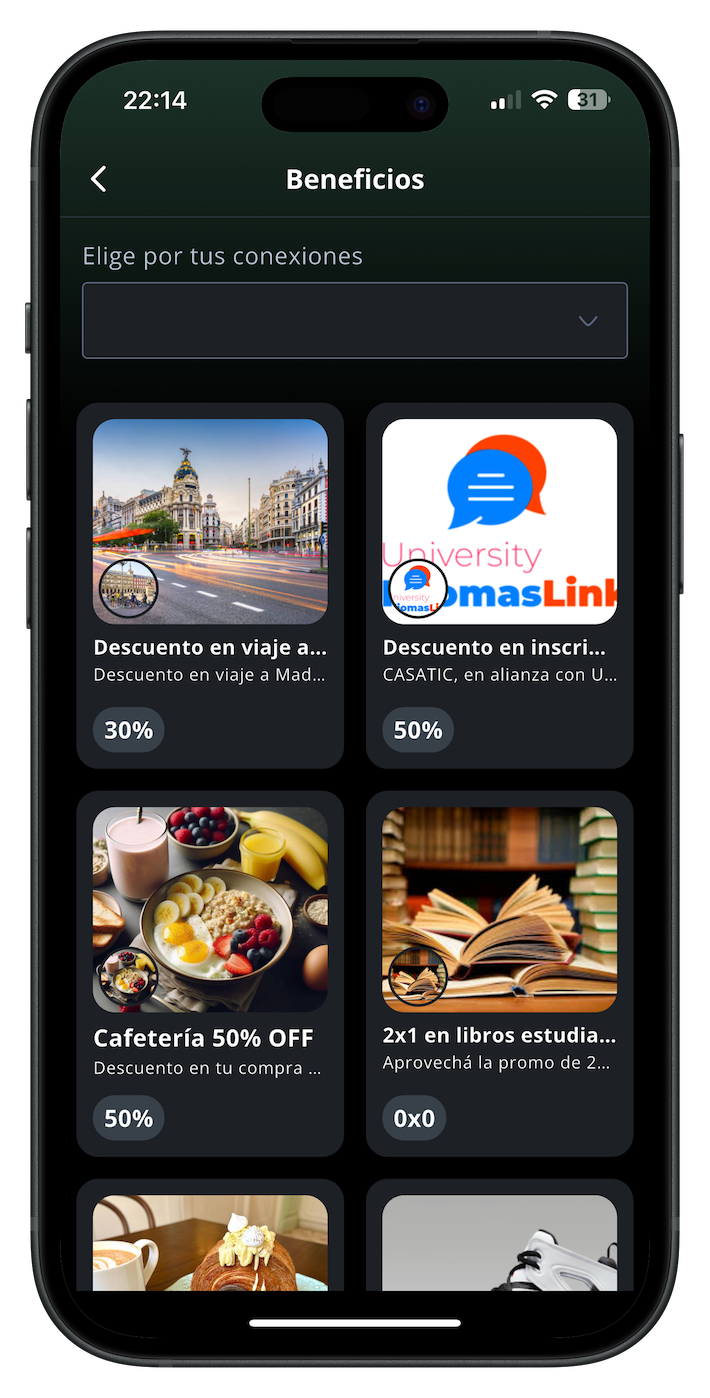
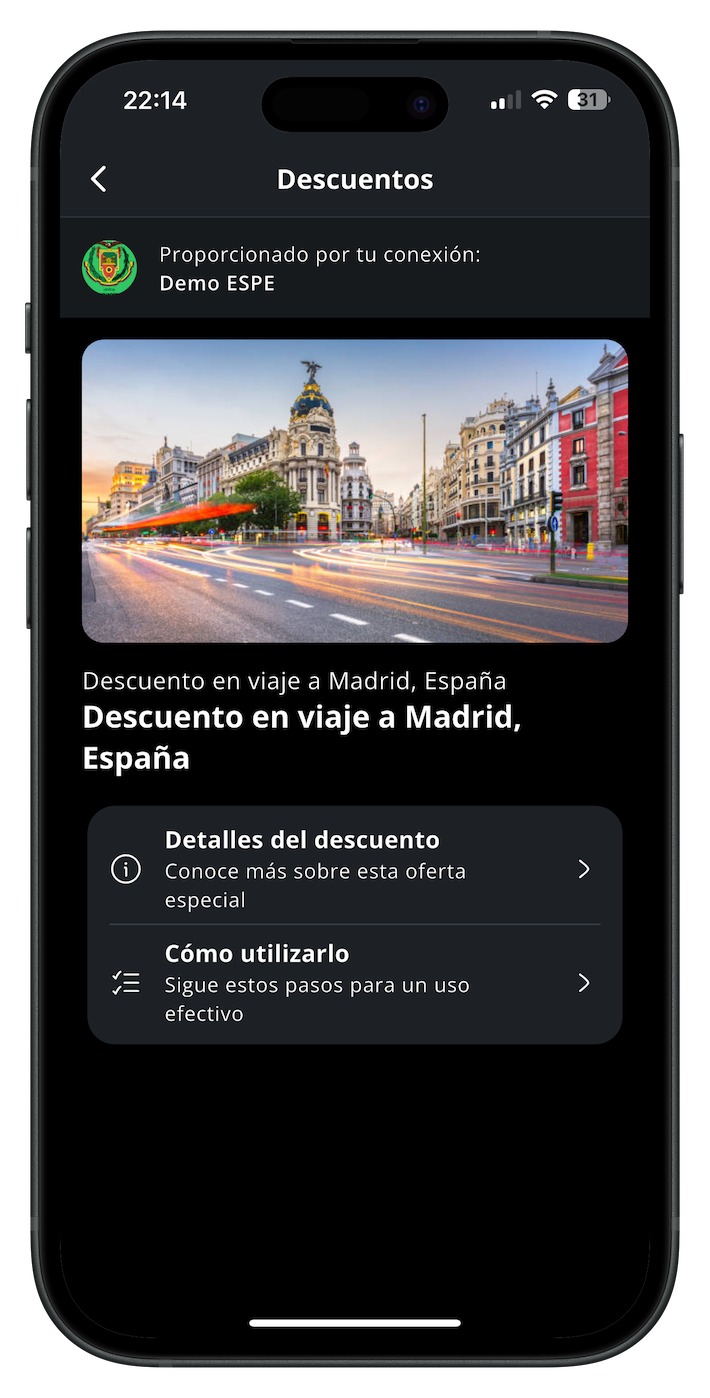
Issue and verify digital benefits instantly through the digital wallet ensuring secure access, traceability, and personalized delivery.
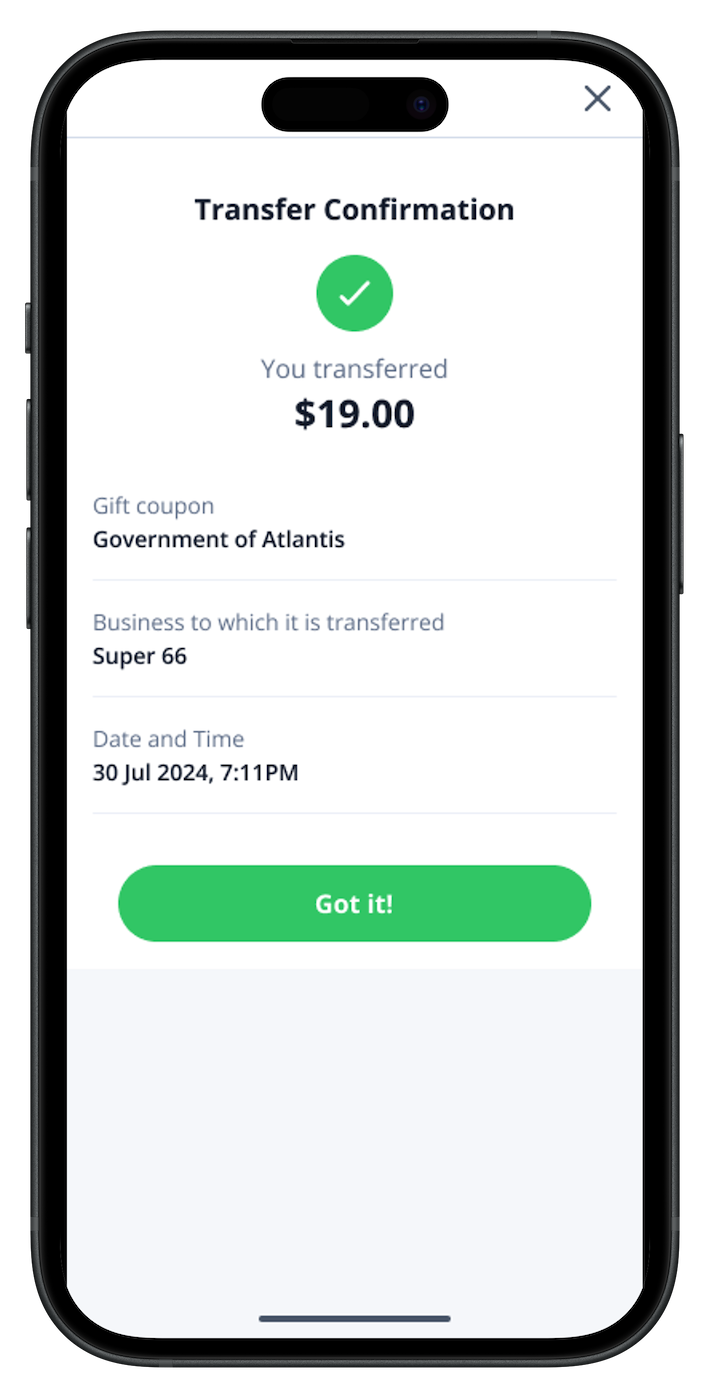
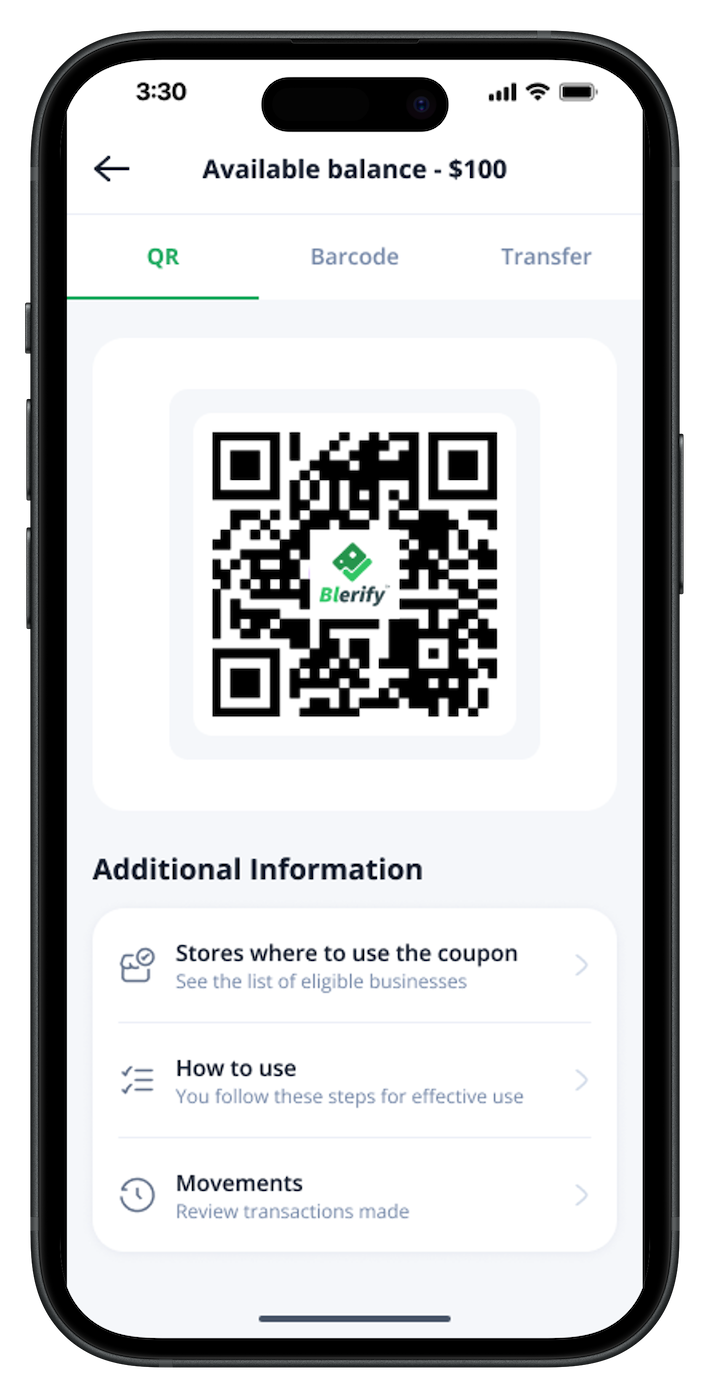
Deliver digital vouchers, gift cards, and payment coupons directly to your users or employees via their digital wallet, ensuring secure, seamless, and instant transactions.
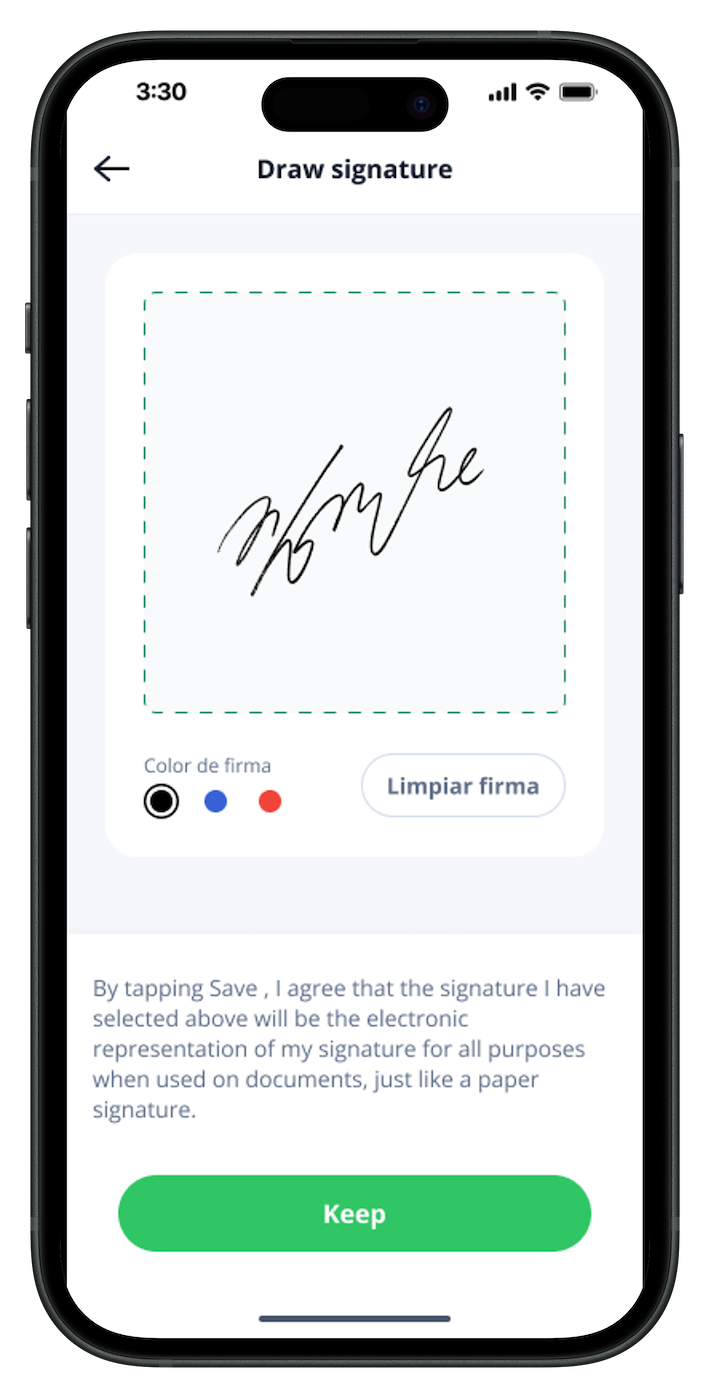

Enable secure, non-repudiable e-signatures through the digital wallet backed by audit trails, cryptographic proof, and certified to meet e-signature requirements.
Complete a purchase
E-Sign a Document
Enroll to a Service
Log in a Website
Enter a Building
Redeem a Benefit















Create digital identity that cannot be spoofed by a fraudster or AI. Breaking the cryptography is computationally impossible – more than 10^77 combinations.

Data in the form of verifiable credentials give users better control over their personal data. Users can share only the required information for an interaction.

Users can access and discover new services and benefits from the comfort of their home, from one single digital channel. Digital credentials saves countless hours for both users and staff.
Explore how you can bring more secure and convenient digital interactions to your users and partners.